Web Malware Security Analysis Tools
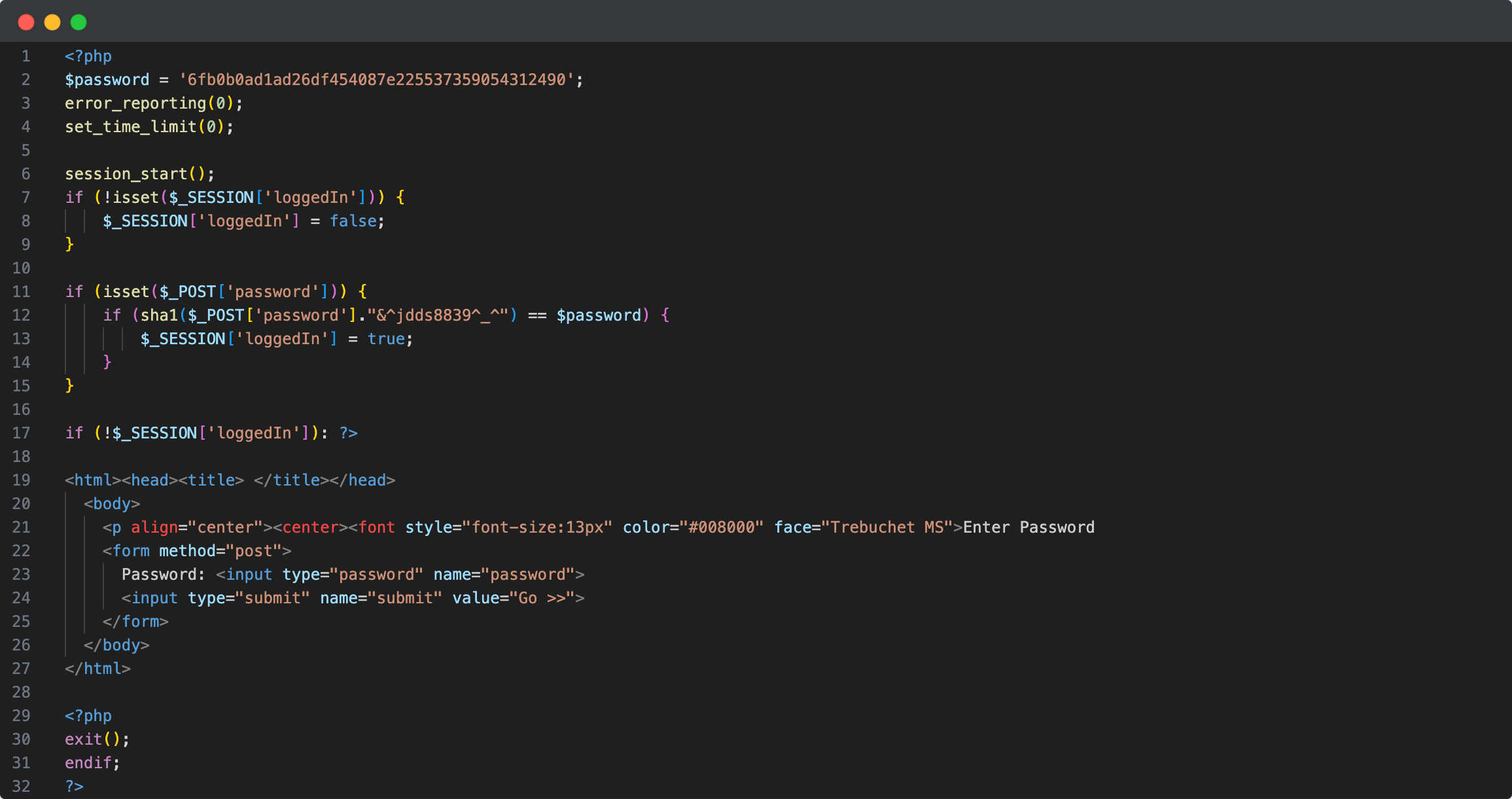
Some time ago, I worked as a security analyst, investigating incidents of website infections, assisting users with remediation, updating the antivirus database, and publishing some samples of malicious software on LinkedIn. During that time, I gathered a significant amount of information. I have decided to publish a post listing the tools that helped me tackle everyday tasks.
I have dealt with website malware over 1,000,000,000 times ![]() Based on this experience, I have prepared some advice. Firstly, in 90% of cases, you can avoid many problems by keeping your site updated and ensuring that you have valid licenses for your plugins, themes, and extensions. Bots analyze your site, detect the CMS, and attempt to exploit vulnerabilities, often targeting popular outdated components or using backdoors that were uploaded with nulled extensions. If you encounter malware on your site, you can use the tools mentioned in this article.
Based on this experience, I have prepared some advice. Firstly, in 90% of cases, you can avoid many problems by keeping your site updated and ensuring that you have valid licenses for your plugins, themes, and extensions. Bots analyze your site, detect the CMS, and attempt to exploit vulnerabilities, often targeting popular outdated components or using backdoors that were uploaded with nulled extensions. If you encounter malware on your site, you can use the tools mentioned in this article.
What do you already have?
If you're using shared hosting or a VPS, you usually have the following:
-
Logs: You can try to investigate how malware was uploaded to your site by examining the webserver logs. Look for the initial entry point. And enable logging if you haven’t already.
-
Backups: You can use backups to restore your site to a previous date when you didn’t have any problems. However, keep in mind that your site may still have vulnerabilities. Only use backups when you’re facing significant issues with site access and functionality. Investigate to identify the source of the problems ;)
-
File managers or FTP: You can manually remove malware using file managers or FTP. Unfortunately, modern sites have a large number of files, making it impractical to check them all manually. Sometimes file managers or FTP tools can also be helpful for restoring the website core. I often used them for WordPress, Joomla, and Drupal.
-
SSH: If you have access to the command prompt, you have a lot of options. For example, you can use ‘grep’ and regular expressions to search for malware strings and remove infected files using those strings. This is a very helpful and powerful tool. I’ve encountered situations where I needed to reload the PHP process via SSH because the malware kept reappearing after deletion. However, not all hosting providers offer SSH access. In such situations, I used Webconsole. I’ve also used webshells like Indoxploit or WSO in certain cases. These tools provide similar and additional functionalities, but be careful, as they are popular shells used by hackers. Pay attention to the source from which you obtained them and review their source code. Remove them as soon as possible after usage.
-
PhpMyAdmin: This tool is often installed on shared hosting. Sometimes malware scripts can be found in your database, particularly in cases of malware redirects. Use PhpMyAdmin to detect and remove these scripts. If your hosting provider doesn’t offer PhpMyAdmin, you can use Adminer. You can read how to remove malware from the database in my post for Virusdie.
Antiviruses and Scanners
-
Quttera - A very powerful tool for externally detecting malware. It helps in finding scripts on webpages and checks if your site is blacklisted. They also provide the Malware Decoder, which is a useful tool for analysts to decode malware and understand how it works.
-
Sucuri - Similar to Quttera, this tool offers external scanning. I sometimes use both Sucuri and Quttera scanners because they use different databases, which increases the chances of finding something new.
-
Virusdie - I worked as a security analyst in this company, and I can confidently say that it’s a great and powerful tool for malware detection, removal, and site protection. It’s useful not only for users but also for security analysts. I’m not advertising, just recommending this tool in case you encounter malware problems on your site.
-
Wordfence - A highly recommended solution that you should use from the first day of installing WordPress. Even if you already have malware, Wordfence can be of great help. It provides a scanner, firewall, and other features that effectively protect your WordPress site.
Of course, this list of tools can be expanded or modified depending on the situation and type of malware. However, I have covered the most frequently used tools by me. I hope this post helps you in solving your malware problems, ensuring your security, or even saving time if you're starting your career as a malware or security analyst.
Bonus: website/domain blacklist providers
Sometimes users may encounter situations where their antivirus or service providers display a notice and block a domain. This often happens even after the website has been cleaned because the blacklist providers haven’t removed the domain name from their database. Users often ask me how they can resolve issues with blacklists. If you want to expedite this process manually, you can determine which provider has blacklisted your site and use the following contact list of popular domain blacklist providers:
- Google Sage Browsing: https://safebrowsing.google.com/safebrowsing/report_error/
- Comodo Valkyrie: https://verdict.valkyrie.comodo.com/contact/us/
- Webroot: https://www.webrootanywhere.com/servicewelcome.asp
- Avira: https://www.avira.com/en/analysis/submit?utm_source=CS&utm_medium=KB
- CyRadar: contact@cyradar.com
- Fortinet: https://www.fortiguard.com/faq/wfratingsubmit
- Sophos: https://support.sophos.com/support/s/?language=en_US#t=SalesforceArticle&sort=relevancy
- CRDF Labs: https://threatcenter.crdf.fr/false_positive.html
- ESET: samples@eset.com or https://support.eset.com/report-a-virus-or-website
- Norton Safe Web: https://safeweb.norton.com/report/show
- Yandex Safe Browsing: https://yandex.com/support/safebrowsing/report-incorrect-diagnosis.xml
- TrendMicro Site Safety Center: https://global.sitesafety.trendmicro.com/
- McAfee: https://service.mcafee.com/?articleId=TS103032&page=shell&shell=article-view or https://www.mcafee.com/consumer/en-us/popup/feedback.html
Please note that this list is not exhaustive, and there may be other providers you need to contact depending on the specific situation.